What is Phishing?
Phishing Explained
As an IT administrator, it’s crucial to ensure that only trusted applications have access to your Microsoft 365 environment. The following steps will guide you through configuring your Microsoft 365 Admin Center to limit user consent for third-party applications, enabling better control over which apps are granted permissions. By implementing these settings, you will reduce the risk of unauthorized applications accessing sensitive organizational data and strengthen your overall security posture.
Navigate to the Identity section.
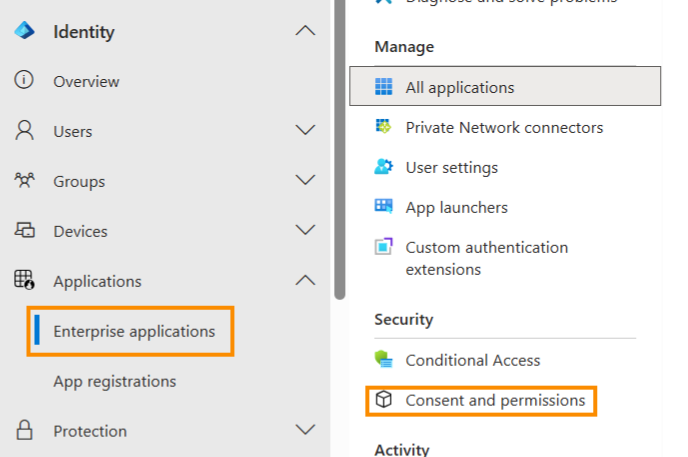
Expand the Applications menu and select Enterprise Applications.
Under Security, click Consent and permissions.
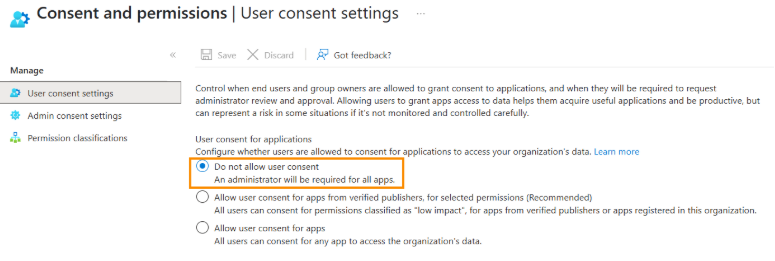
In the User consent settings, select Do not allow user consent. An administrator will be required for all apps.
Click Save to apply the changes.
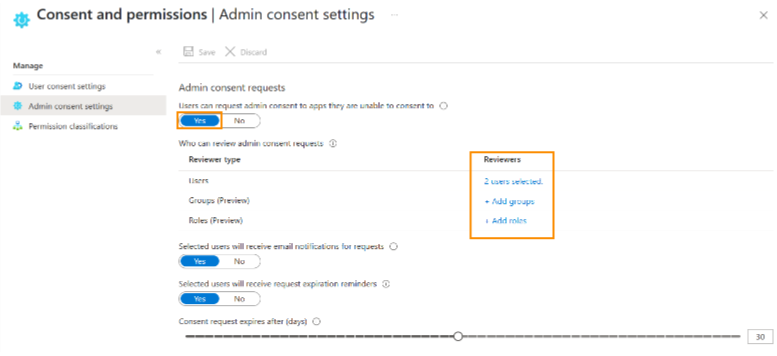
Under Manage, click Admin consent settings.
Set Users can request admin consent to apps they are unable to consent to to Yes.
Select Add user or group to assign individuals who will be responsible for reviewing and approving application requests.
By following these steps, you'll be able to effectively control and monitor third-party application access, ensuring a more secure Microsoft 365 environment for your organization.