Process
Phishing Training That Works
Our simulations resemble real-world attacks. By enticing targets in the same manner a threat actor would deploy, leading them down a path of information disclosure, and then following any failure with a training moment, we educate the target to prevent real breaches in the future.
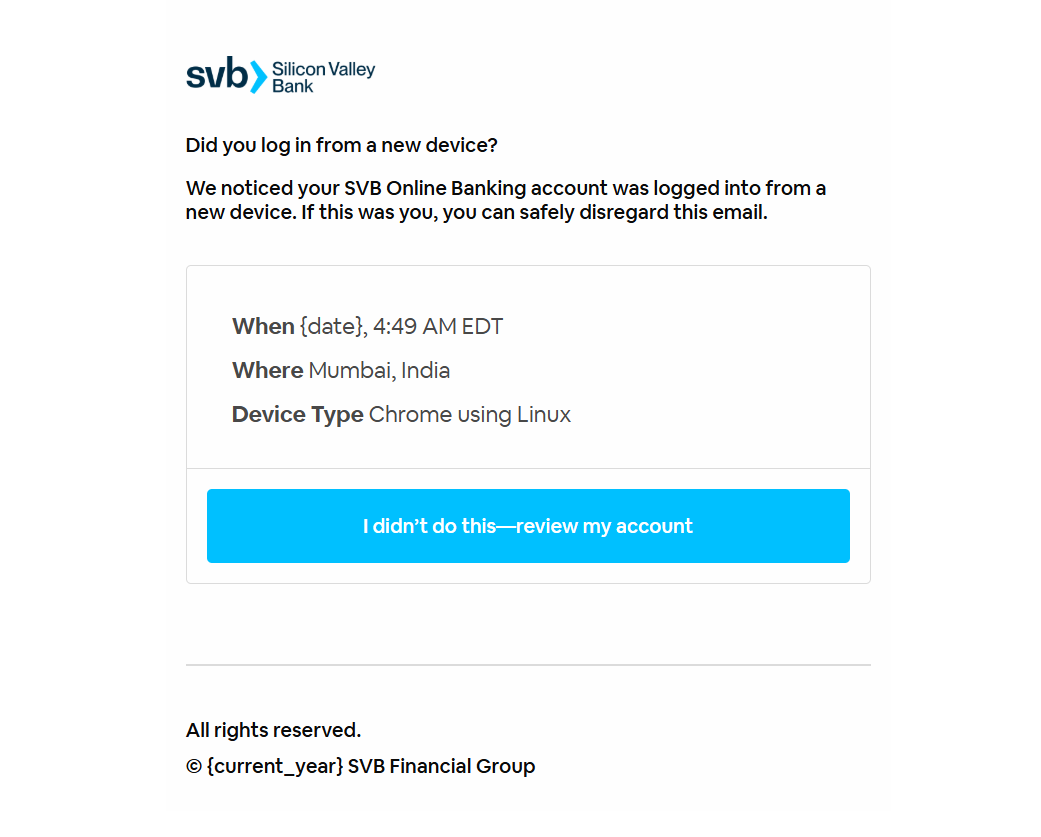
Phishing Email
A compelling phishing email designed to entice the target is sent.
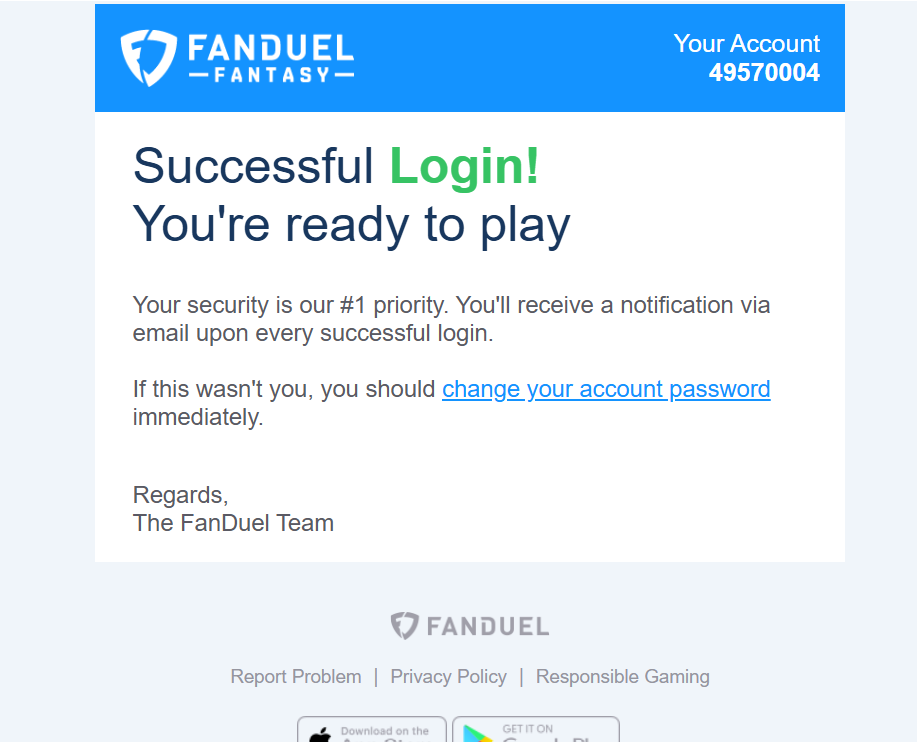
Hooked
The user interacts with the email and is reeled into the simulation.
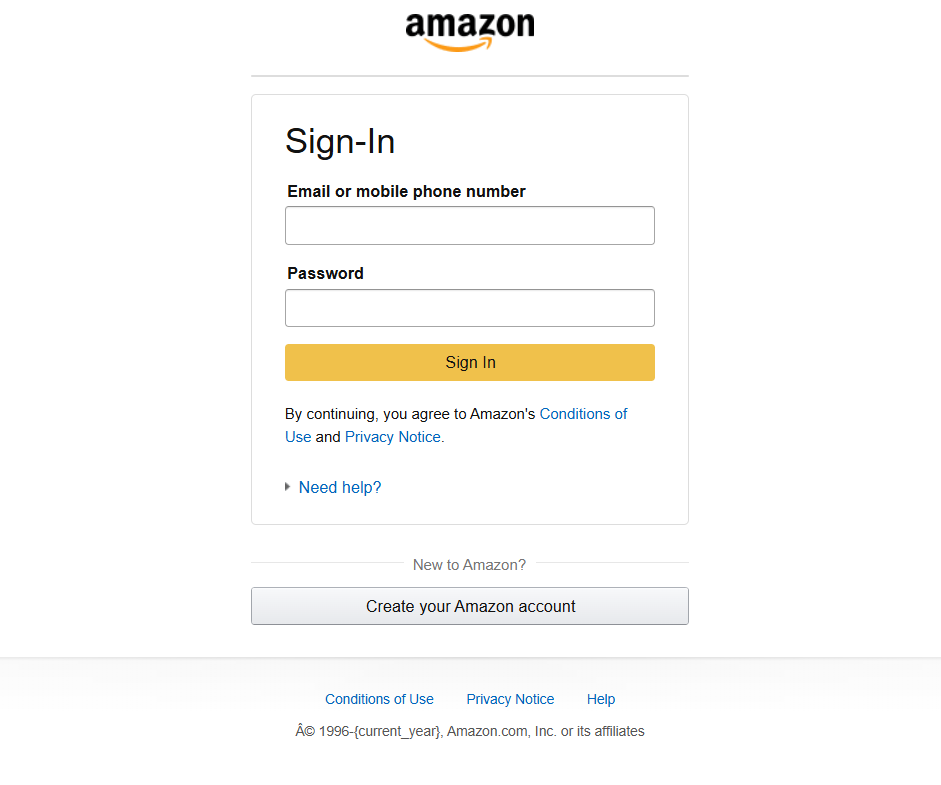
Landing Page
A curated landing page is presented with intent to gather sensitive information.
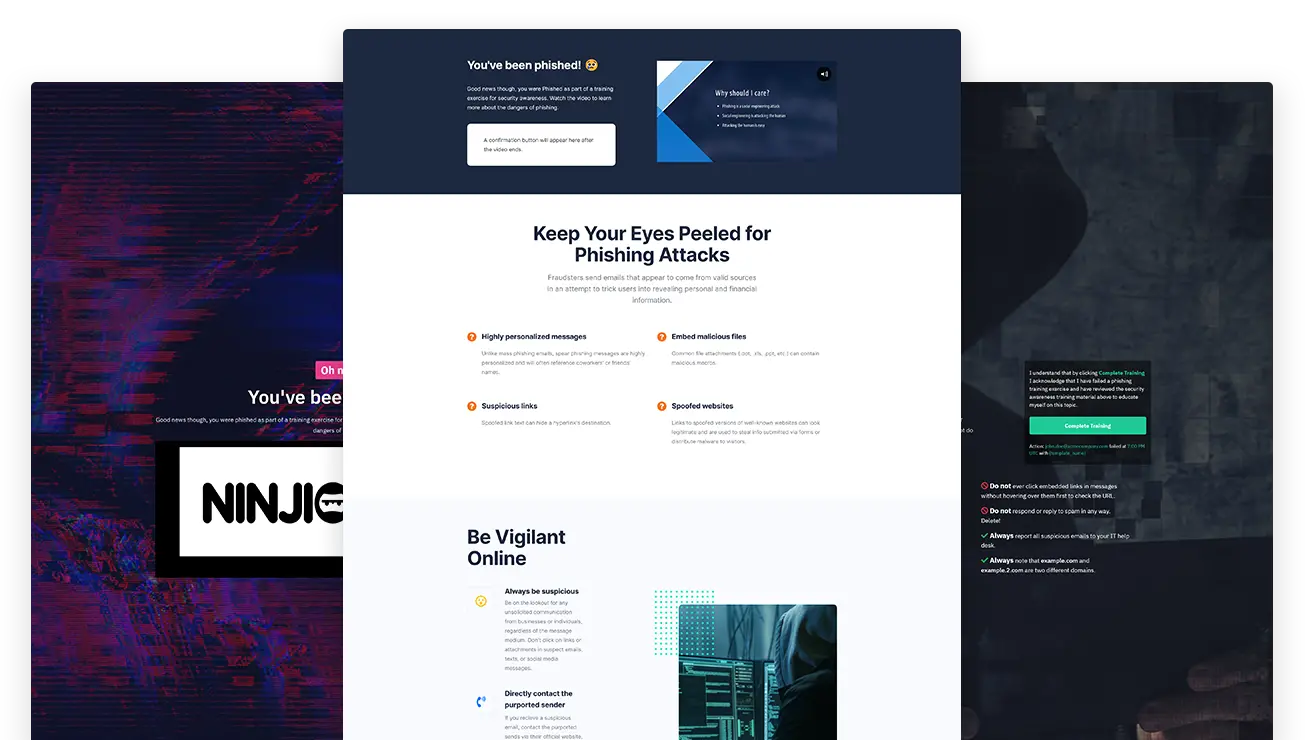
Training Moment
The target is notified of their error and educated to prevent future phishing email failures.
Phishing Email
The human element has been, and always will be, one of the weakest links in cybersecurity. Our expansive template library contains hundreds of realistic phishing emails.
Hooking the Target
Our designs lure the target deeper into our phishing simulation, either leading them to landing pages for further data extraction or directly into remedial training.
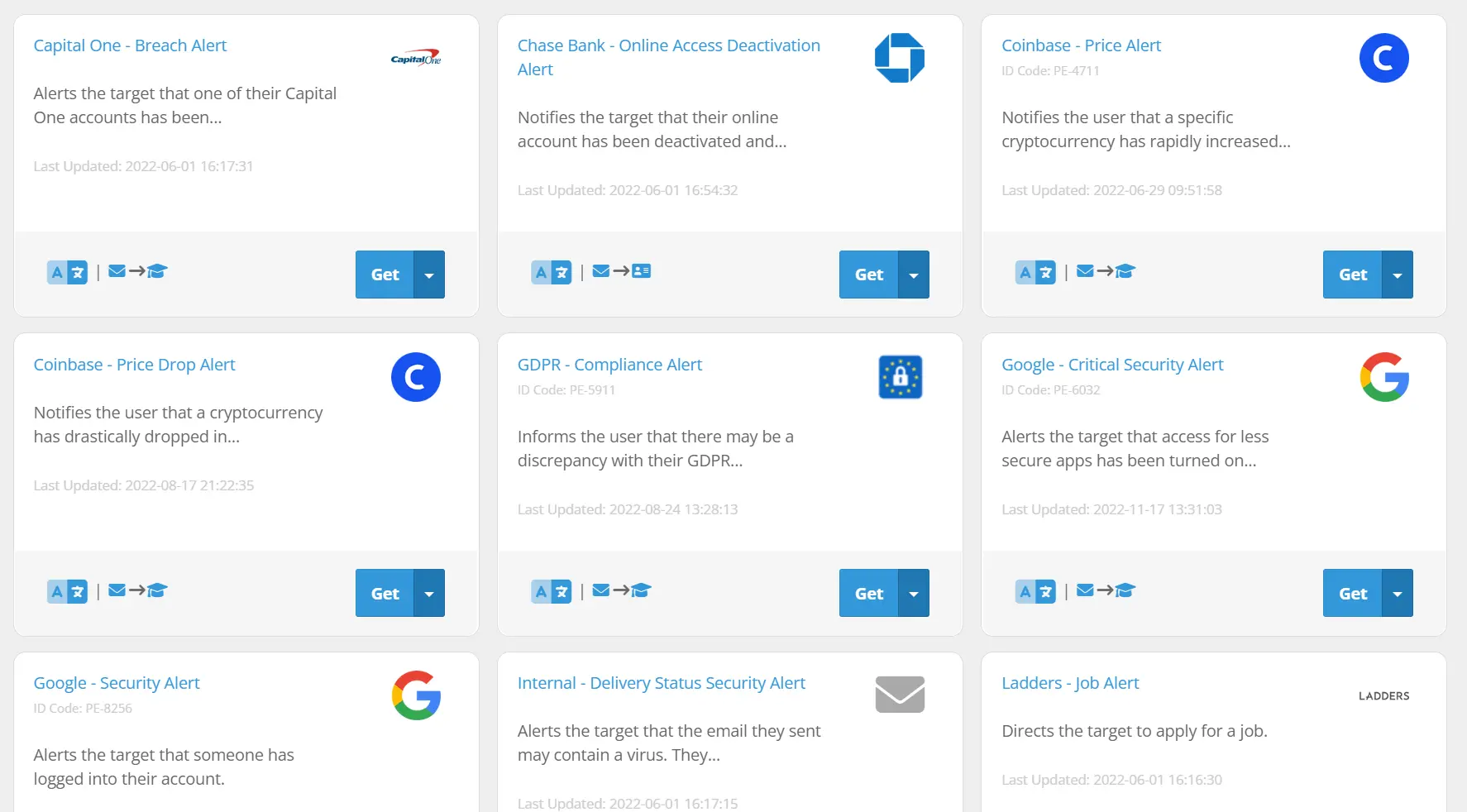
Examples
Templates you might come across...
Below are samples of our Template Library's phishing emails and landing pages. Our expansive library has hundreds of templates to choose from to fit every scenario.
Landing Page
We provide a large variety of curated phishing landing pages. Typically, a mimicked login page or other data entry page is presented to the target to extract sensitive information or credentials just like a real phishing attack would.

Training Moment
Some employees need additional training. By training with our phishing simulator, these employees are easily identified and failures can be automatically assigned additional cybersecurity training. With auto-enrollment, the burden of assigning training is minimized. Employees who fail a phishing test are presented with a Training Moment and assigned cybersecurity training courses while the PhishingBox system monitors their training progress.