KillPhish
Email scanning and reporting for your mobile devices, tablets, and computers
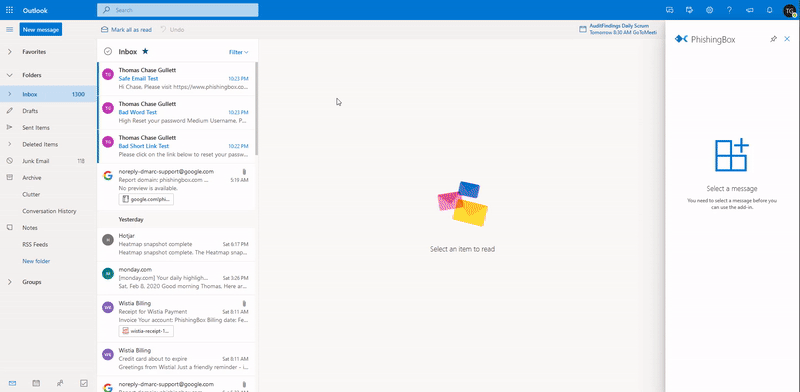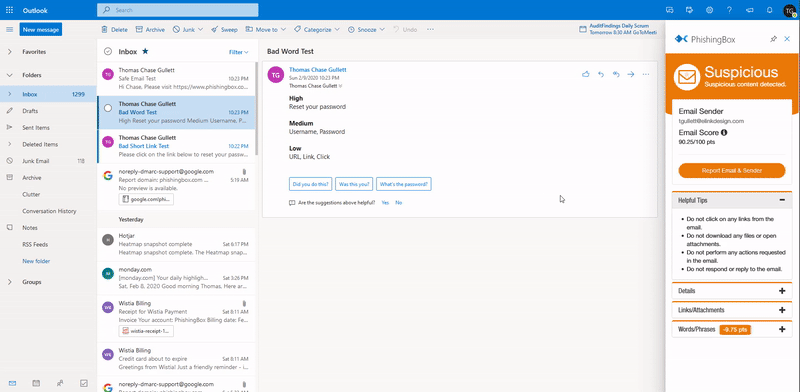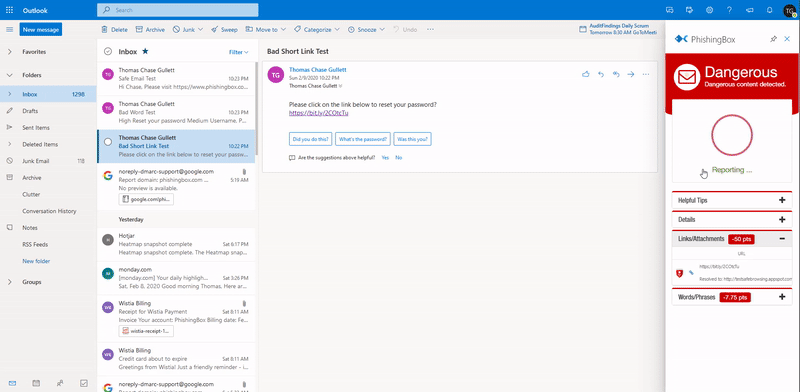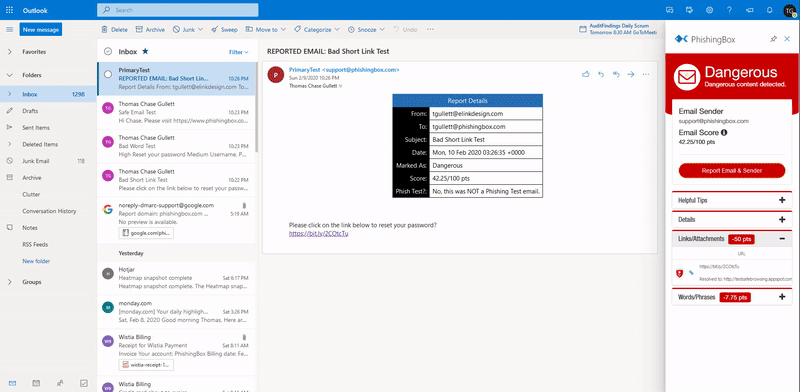
Scanning & Reporting Email Threats
KillPhish™ is an advanced email threat protection add-in for Microsoft 365. It scans known threats on Windows, Mac/iOS, and Android for Outlook Desktop, Web, and Mobile. It enables reporting phishing and other types of threats (Google and Microsoft add-ins). Each inbox's risk profile is unique and KillPhish can help expose security threat signs.
KillPhish™ AI
Harnessing the power of Artificial Intelligence to scan and assess the safety of emails. Keep your email security in check on your mobile devices, tablets, and computers.

Net Reporter Score
Learn how to help score and rank user risk level in your organization.
KillPhish™ helps users learn what to look for using our email scoring method.
-

Microsoft
-

Google Workspace
-

Apple
-

Android
Features
Powered by AI
KillPhish™ harnesses the power of Artificial Intelligence to analyze and assess potential threats with reliable accuracy.
Phishing Simulator
KillPhish™ add-in seamlessly integrates with our Phishing Simulator to produce additional reporting with Net Reporter Scores.
Easy to Deploy
KillPhish™ reporting button works with Google and Microsoft (inbox scanning feature available for Microsoft only).
Live Inbox Training
KillPhish™ helps users learn what to look for using each email as a learning opportunity, combined with human risk management.
Extend the Endpoint
KillPhish™ pushes your endpoint protection even further and helps users better determine a real threat versus legitimate emails.
Multiple Sources
KillPhish™ gathers IP addresses, domains, email addresses, keywords, and other threat types from different sources.
Net Reporter Score™
With the Net Reporter Score, organizations have a simple-to-understand metric for measuring security awareness.
Frequently Asked Questions
If any questions you have remain unanswered, feel free to contact us.
Additional Resources
PhishingBox Ecosystem
This brochure provides an overview of the PhishingBox security awareness ecosystem.
DownloadBusiness Case
This document provides an overview of the benefits of using PhishingBox's Phishing Simulator and ongoing cybersecurity training.
DownloadPrevention Checklist
This document outlines controls that should be implemented to prevent or minimize phishing attacks.
Download