
Introduction
Password managers like LastPass, 1Password, and Bitwarden have become essential tools for both individuals and organizations, safeguarding countless credentials behind one master key. Unfortunately, their trusted reputations and the sensitive data they protect have made them prime targets for phishing campaigns. Cybercriminals are increasingly impersonating password manager brands in sophisticated scams, knowing that stealing a single set of master credentials can unlock a jackpot of accounts【1】【2】. In recent years (2025–2026), we’ve seen a rise in real-world phishing attacks that masquerade as legitimate communications from these password manager services. These attacks prey on user trust and urgency, leveraging social engineering to bypass security measures.
This report delves into notable recent examples, the attacker techniques employed, how social engineering tricks users (even those with multi-factor authentication), the consequences of such breaches, and how these threats are evolving. It also outlines how proactive defenses such as phishing awareness training, simulated phishing tests, and human risk management tools (for example, platforms like PhishingBox) can help organizations of all kinds (from IT and security teams to finance, HR, and beyond) mitigate the risk.
Recent Examples of Password Manager Phishing Attacks
Real-world incidents demonstrate how convincingly attackers can pose as password manager providers. Below are several recent phishing campaigns impersonating password managers, showing the variety of lures and tactics used:
- “Vault Backup” Scam (LastPass – Jan 2026): An active campaign targeted LastPass customers with emails claiming LastPass needed users to “securely backup your vault” within 24 hours due to urgent maintenance【3】. The phishing emails, sent during a U.S. holiday weekend, used official-sounding subject lines like “Protect Your Passwords: Backup Your Vault (24-Hour Window)” to create panic and rushed action【3】. Victims who clicked the provided “Create Backup Now” link were taken to a fake site (hosted on Amazon infrastructure and then redirecting to a lookalike domain mail-lastpass[.]com) that stole their master password【4】【5】. LastPass confirmed it was not conducting any such vault backup request, and described the emails as a malicious ploy exploiting urgency【5】.
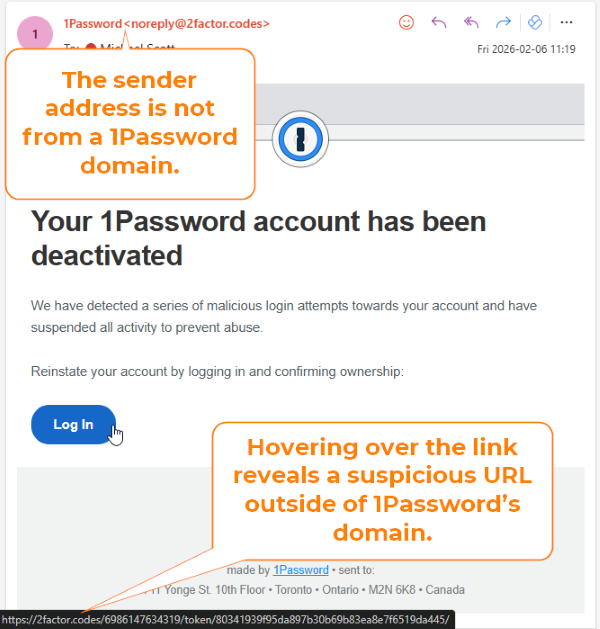
- Phony “Watchtower Breach Alert” (1Password – Oct 2025): In another case, scammers impersonated 1Password’s security notification feature (called “Watchtower”). Emails told users that their 1Password account password was found in a data breach, a frightening prospect since that password unlocks their entire vault【1】. The message urged immediate action: “Secure my account now.” Everything from the branding to the security advice looked legitimate, but the included link sent users to a fake 1Password login page (at a typosquatted domain onepass-word.com) designed to capture credentials【1】【6】. The sender’s email (watchtower@eightninety.com) and the odd hyphen in the domain were subtle red flags【1】. This convincing breach alert scam nearly tricked even a Malwarebytes cybersecurity employee, illustrating how well-crafted these impersonation emails can be【1】.
- Fake “Secure App Update” Malware (LastPass & Bitwarden – Oct 2025): A widespread phishing campaign targeted users of both LastPass and Bitwarden by sending fake security notices that the companies had been hacked【7】. The emails urged recipients to “download a new, more secure desktop application,” presented as an urgent update to protect their vaults. In reality, the download was malicious. Those who complied unwittingly installed a remote monitoring/remote access chain using Syncro and ScreenConnect tooling, handing attackers broad control of the victim’s computer【7】. LastPass publicly refuted the hack claims and emphasized the messages were a social engineering attempt exploiting fear【7】. Notably, the phishers used lookalike sender domains such as hello@lastpasspulse.blog and hello@bitwardenbroadcast.blog to appear credible【7】. By referencing a (fictional) vulnerability in “outdated .exe” installers and timing the campaign over a long holiday weekend, the attackers made the ruse sound technically plausible and hoped to evade quick detection【7】. This campaign shows that attackers are not just after passwords and will hijack endpoints for broader compromise【7】.
- “Legacy Access” Deception (LastPass – 2024 & 2025): An ongoing series of attacks by a group dubbed “CryptoChameleon” has repeatedly impersonated LastPass with creative lures【8】. By October 2025, this group escalated to an elaborate “family emergency” scam: users received emails claiming a family member had requested access to their vault (part of LastPass’s Emergency Access / inheritance process)【8】【9】. The phishing email included an official-sounding “legacy access” request and asked the user to upload a death certificate, all fake but designed to alarm users【8】. If the user interacted further, they were directed into a credential-harvesting flow intended to capture the master password【8】【9】. Some reporting also noted attackers used phone calls as part of the social engineering, pressuring targets to follow instructions【10】. LastPass warned that no real support agent would ever ask for a master password or verification in this manner【8】.
- Malicious Ads Impersonating Bitwarden (Nov 2024): Not all phishing begins with an email. In late 2024, Bitdefender researchers uncovered a malvertising campaign on Facebook where attackers ran ads masquerading as Bitwarden【11】. The sponsored posts warned that “Your Passwords Are at Risk!” and urged people to update their Bitwarden browser extension immediately【11】. The ad led to a phony destination that attempted to trick users into installing a malicious extension by abusing developer-mode / sideload patterns, bypassing normal safety expectations【11】. Once installed, the extension sought broad permissions consistent with credential theft and session hijacking objectives【11】. This attack shows how phishing impersonation can extend beyond email to ads and social media, leveraging trusted platforms to fool users into compromising their own accounts【11】.
- Example: LastPass and multiple outlets described phishing emails urging users to “Create Backup Now” under the guise of urgent maintenance. Attackers often use official logos, familiar layouts, and urgent warnings (e.g., “Action Required: 24 Hours”) to pressure victims into clicking without thinking【3】【5】.
- Each of these cases underscores a common theme: attackers are leveraging the trust users place in password managers. By copying the branding, tone, and even security features of these services, phishers make their traps highly convincing. Next, we analyze the tactics behind these impersonation attacks in more detail.
Attacker Techniques: How These Scams Work
- Convincing Lures and Pretexts: The phishers design scenarios that appear to come from the security-conscious password manager vendor. Common lures include security alerts (e.g. “we detected your password in a breach” or “urgent security update required”) and maintenance notices (“backup your vault or lose access”)【1】【3】. These messages tap into users’ fear of unauthorized access or losing their data. Importantly, the requests mimic plausible actions a password manager might ask for, such as installing an update, changing a password, or verifying account status. By referencing real features (like 1Password’s Watchtower breach monitoring or LastPass’s Emergency Access / inheritance flow), attackers make the scam feel legitimate【1】【8】. In one case, the fraudulent email cited “weaknesses in older .exe installations” to add credibility for tech-savvy users【7】. The attackers craft their emails with professional branding and urgent language that lowers the victim’s guard【5】.
- Brand Spoofing & Lookalike Domains: A hallmark of these campaigns is the use of spoofed sender addresses and fake domains that closely resemble the real brands. Attackers register lookalike domains or subdomains, for example onepass-word.com vs. the real 1password.com, or mail-lastpass[.]com to appear affiliated with LastPass【1】【5】. In the 2025 fake breach alert scam, the phishing link also used a legitimate email tracking/redirect service before landing on the fake domain, which can make detection harder【1】. Some attackers hosted content on trusted cloud platforms to lend legitimacy, and then redirected victims to the impersonation site【5】. By abusing well-known services and crafting domains that pass a casual glance, phishers make it technically tricky for email filters to block messages and for users to spot the fraud【5】.
- Urgency and Fear Tactics: Nearly all these impersonation emails include a strong element of time pressure or emotional urgency. Threat actors commonly warn of dire consequences if the user doesn’t act immediately, such as “24-hour window” or “account will be compromised”【3】【5】. This tactic is deliberate: creating a false sense of urgency is one of the most effective social engineering tricks in phishing【12】. Additionally, some campaigns were timed strategically, launching over weekends or holidays when IT staff might be slower to respond【3】【5】.
- Abuse of Legitimate Tools and Channels: Modern phishing schemes often piggyback on legitimate infrastructure to evade detection. The fake “secure desktop app” campaign used widely known remote tooling (Syncro/ScreenConnect) in a malicious way, blending in with normal IT activity【7】. We also saw Facebook’s ad network abused, where sponsored ads were used as the entry point for a fake Bitwarden update lure【11】. By operating through reputable channels, attackers make their traps harder to identify and block【11】.
- Use of Breached Data & Personalization: Some of these phishing campaigns may be aided by data from previous breaches and by the broad public awareness of breaches. Attackers can target known customer emails and tailor language to match ongoing news and common security anxieties, increasing believability. (This is a common pattern noted across large breach datasets and threat reporting.)【13】
Social Engineering to Bypass MFA and User Vigilance
- Exploiting Trust in Authority: Many phishing emails impersonating security services carry an implicit authority, appearing to come from a “Security Team” or customer support. Attackers rely on trust in the vendor brand, especially when the message frames itself as protective or urgent【5】.
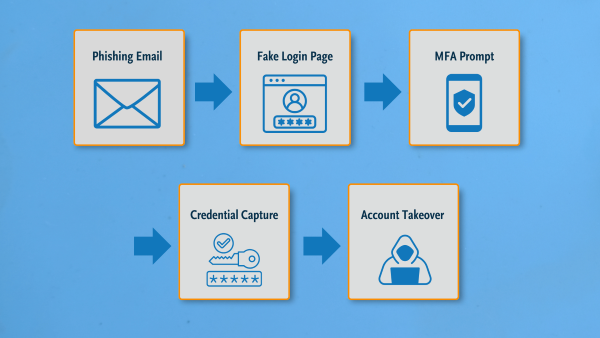
- Multi-Channel Phishing (Voice and Email): Combining channels, such as vishing plus email phishing, is a growing tactic to bypass safeguards. Reports tied to the CryptoChameleon activity describe a multi-touch approach that can include email plus additional pressure tactics【8】【10】. This can defeat MFA if the user is tricked into sharing an OTP or approving a push prompt.
- Real-Time MFA Capture: Even without a phone call, sophisticated phishing sites can proxy the login flow and capture MFA in real time (commonly described as adversary-in-the-middle / real-time phishing). Guidance on MFA threats and bypass techniques is discussed in government security advisories on defending MFA implementations【14】.
- Passkey and “Passwordless” Tricking: As passkeys and passwordless authentication become more common, attackers adapt by exploiting user confusion and setup workflows. LastPass specifically referenced attacker interest in passkeys and related social engineering themes in its threat intel coverage of the CryptoChameleon campaign【8】.
- Psychological Manipulation: Fear, urgency, helpfulness, and curiosity remain core levers. Government anti-phishing guidance consistently emphasizes avoiding link-clicking impulses and verifying messages independently【12】.
Impact: Stolen Credentials, Account Takeovers, and Organizational Risk
- Complete Credential Theft: If the phishing succeeds in capturing a user’s master password (and any 2FA factor), the attacker can access every login and secure note stored in the vault, enabling rapid expansion of compromise across many accounts【8】【9】.
- Immediate and Long-Term Account Takeovers: With vault access, attackers prioritize high-value accounts (email, financial platforms, cloud services) and can trigger cascading compromises across personal and work systems.
- Organizational Breach and Lateral Movement: If an enterprise password manager account is compromised, attackers can gain valid credentials to internal systems, bypassing many perimeter defenses and enabling deeper intrusion. Large-scale breach research continues to show significant financial impact from security incidents, with IBM reporting a global average breach cost of $4.44 million in its 2025 report【15】.
- Reputation and Trust Damage: Impersonation scams can erode trust in legitimate security alerts and complicate real incident communications.
- Personal Fallout: Victims often face extensive recovery work, rapid password changes across dozens of services, and potential identity theft outcomes.
An Evolving Threat Landscape (2025–2026)
- More Polished, More Convincing (Thanks to AI): Attack content is increasingly realistic and scalable. 1Password and multiple outlets have discussed how AI is “supercharging” phishing and the need for stronger phishing-resistant cues and protections【16】.
- Targeted and Personalized Attacks: Attackers refine narratives and reuse successful kits/campaign motifs across waves of activity (as seen with CryptoChameleon / password manager impersonation)【8】.
- Multi-Vector Campaigns: Email, ads, SMS, and voice all contribute to modern “omni-channel” deception【11】.
- Bypassing New Security Measures: Vendors are responding with anti-phishing protections. For example, 1Password introduced extension-based phishing warnings to help users detect URL mismatches and reduce credential entry on lookalike sites【17】.
- • Greater Scale through Automation: Criminal ecosystems continue to operationalize phishing with scalable infrastructure and repeatable playbooks (as reflected in recurring campaign patterns documented by major security outlets)【7】.
- Focus on High-Value Outcomes: Many campaigns aim for broader compromise beyond credential theft, including endpoint hijacking and persistence using abused legitimate tooling【7】.
Mitigation Strategies: Training, Simulation, and Risk Management

Defending against these campaigns requires a layered approach. Technical controls matter, but social engineering targets people directly. Key mitigation strategies include:
- Continuous Security Awareness Training: Users should learn current attacker tactics and verification habits. Government guidance emphasizes not clicking unexpected links, validating senders, and reporting suspicious messages【12】. NIST provides frameworks for building and improving organization-wide security awareness and training programs【18】【19】.
- Phishing Simulations: Running controlled simulations helps identify which lures and user groups are most at risk and provides safe, teachable moments. (Use of simulations is widely recommended as part of mature awareness programs and aligns with NIST learning-program guidance.)【19】
- Human Risk Management & Monitoring: Track who clicks, who reports, and how behavior changes over time. NIST guidance explicitly discusses measurement and ongoing program improvement for training initiatives【18】【19】.
- Implementing Technical Safety Nets: Strengthen anti-phishing defenses: email security controls, link analysis, domain monitoring, and phishing-resistant MFA. CISA guidance explains threats to MFA (including push bombing and phishing) and how to move toward phishing-resistant MFA methods【14】.
- Policies and Incident Response Plans: Establish clear policies (for example, “We will never ask for master passwords via email”) and encourage fast reporting. CISA provides practical guidance on recognizing and reporting phishing【12】.
- Executive and High-Privilege Focus: Executives and admins are high-value targets. Ensure leadership participates in training and receives role-relevant content, consistent with role-based training principles in NIST guidance【18】【19】.
In conclusion, as phishing campaigns impersonating password managers grow more elaborate, defenses must become more human-centric and proactive. By combining education, realistic practice, and supportive security tools, organizations can significantly reduce the risk that an employee will be duped by these scams.
Sources
[1] Malwarebytes – Phishers target 1Password users with convincing fake breach alert
https://www.malwarebytes.com/blog/news/2025/10/phishers-target-1password-users-with-convincing-fake-breach-alert
[2] CSO Online – Phishers turn 1Password’s Watchtower into a blind spot
https://www.csoonline.com/article/4068754/phishers-turn-1passwords-watchtower-into-a-blind-spot.html
[3] SC Media – LastPass warns of vault backup phishing emails (Jan 2026)
https://www.scworld.com/news/lastpass-warns-of-vault-backup-phishing-emails
[4] BleepingComputer – Fake LastPass emails pose as password vault backup alerts (Jan 2026)
https://www.bleepingcomputer.com/news/security/fake-lastpass-emails-pose-as-password-vault-backup-alerts/
[5] LastPass blog – New Phishing Campaign Targeting LastPass Customers (Jan 2026)
https://blog.lastpass.com/posts/new-phishing-campaign-targeting-lastpass-customers
[6] (Covered within Malwarebytes reporting; URL mismatch + redirect details)
https://www.malwarebytes.com/blog/news/2025/10/phishers-target-1password-users-with-convincing-fake-breach-alert
[7] BleepingComputer – Fake LastPass, Bitwarden breach alerts lead to PC hijacks (Oct 2025)
https://www.bleepingcomputer.com/news/security/fake-lastpass-bitwarden-breach-alerts-lead-to-pc-hijacks/
[8] LastPass blog – Possible CryptoChameleon Social Engineering Campaign… (Oct 2025)
https://blog.lastpass.com/posts/possible-cryptochameleon-social-engineering-campaign-targeting-lastpass-customers-and-more
[9] BleepingComputer – Fake LastPass death claims used to breach password vaults (Oct 2025)
https://www.bleepingcomputer.com/news/security/fake-lastpass-death-claims-used-to-breach-password-vaults/
[10] PC Gamer – LastPass warns of a new phishing campaign involving death certificates… (Oct 2025)
https://www.pcgamer.com/software/security/lastpass-warns-of-a-new-phishing-campaign-involving-death-certificates-and-a-nefarious-email-that-demands-you-reply-to-it-if-youre-not-dead/
[11] Bitdefender Labs – Malicious Facebook Ad Campaign Targeting Bitwarden Users (Nov 2024)
https://www.bitdefender.com/en-us/blog/labs/inside-bitdefender-labs-investigation-of-a-malicious-facebook-ad-campaign-targeting-bitwarden-users
[12] CISA – Recognize and Report Phishing
https://www.cisa.gov/secure-our-world/recognize-and-report-phishing
[13] Verizon – 2025 Data Breach Investigations Report (PDF)
https://www.verizon.com/business/resources/T510/reports/2025-dbir-data-breach-investigations-report.pdf
[14] CISA – Implementing Phishing-Resistant MFA (PDF)
https://www.cisa.gov/sites/default/files/publications/fact-sheet-implementing-phishing-resistant-mfa-508c.pdf
[15] IBM – Cost of a Data Breach Report 2025
https://www.ibm.com/reports/data-breach
[16] 9to5Google – 1Password will now warn you of potential phishing scams… (Jan 2026)
https://9to5google.com/2026/01/22/1password-phishing-protection/
[17] The Verge – 1Password is introducing a new phishing prevention feature (Jan 2026)
https://www.theverge.com/tech/864980/1password-security-phishing-attack-prevention-password-browser-extension-scammers
[18] NIST SP 800-50 – Building an IT Security Awareness and Training Program
https://tsapps.nist.gov/publication/get_pdf.cfm?pub_id=151287
[19] NIST SP 800-50r1 – Building a Cybersecurity and Privacy Learning Program
https://csrc.nist.gov/pubs/sp/800/50/r1/final






