Originally published February 2024 — updated November 2025 with new Facebook phishing campaigns targeting personal and business accounts.

Facebook remains one of the most frequently targeted platforms for phishing and account-takeover attacks. Cybercriminals continue to develop new techniques to impersonate Meta, steal login credentials, and compromise both personal and business accounts. This November 2025 update highlights the latest Facebook phishing scams identified by security researchers—and provides actionable steps to protect your organization.
New Facebook Phishing Scams (2025 Update)
1. Redirect Abuse Using Facebook’s Warning Pages
Recent research uncovered large-scale attacks using Facebook’s own external link warning pages to enhance credibility. Attackers build redirect chains that start from Facebook’s legitimate interface, making users more likely to trust the link.
How the Scam Works
- Attackers register benign-looking domains such as thebeachvilla.co.za or omniotech.co.uk.
- These domains host scripts that redirect users through Facebook's warning page.
- After the user clicks “Continue,” they land on a fake Facebook login page designed to steal credentials.
- After harvesting credentials, the victim is redirected to the real login page to reduce suspicion.
- Campaigns are highly customized by language and urgency, often claiming “unusual activity detected.”
Why This Matters
This tactic blends platform-level trust with social engineering, making the attack harder to spot. Even users who are security-conscious may assume the link is safe because Facebook generated the warning dialog.
2. Fake Facebook Business Pages Flooding Users With Phishing Messages
Another major development is a surge in phishing attacks targeting Facebook Business Pages, advertisers, and social media managers—an area that attackers increasingly view as high-value.
What Security Researchers Found
- Attackers create new Facebook Business Pages that mimic official Meta branding.
- These pages then send phishing emails from the legitimate domain facebookmail.com.
- Messages falsely claim account violations, ad policy issues, or eligibility for benefits like “free ad credit.”
- One campaign generated over 40,000 phishing emails, with individual businesses receiving thousands in a short time.
Why Businesses Are Vulnerable
Social media managers and advertisers rely on Facebook for daily operations, so urgent messages about policy or ad spend feel believable. The use of Meta’s real email domain further increases trust.
Common Facebook Phishing Scams Still Active
Even as attackers adopt new methods, many longstanding tactics continue to affect users:
- Compromised accounts posting emotionally charged links (“I can’t believe what happened…”) that lead to credential-harvesting sites.
- Direct messages from compromised friends encouraging users to click malicious links.
- Fake security alerts claiming someone else attempted to log in.
- Giveaway, prize, or gift card scams impersonating popular brands.
These persistent tactics continue to succeed because they rely on urgency and familiarity.
The Risks: Why Facebook Phishing Is More Than Just a Social Media Problem
A compromised Facebook credential can lead to:
- Access to Instagram, Messenger, and connected apps
- Control over business pages, ad accounts, and audiences
- Unauthorized ad spending or scams targeting customers
- Social engineering attacks against employees
- Lateral movement into work-related systems via reused passwords
For organizations, the business-page phishing wave is especially dangerous, as attackers often aim to monetize accounts or distribute scams at scale.
How to Protect Users and Organizations From Facebook Phishing
1. Enable Multi-Factor Authentication (MFA) on All Accounts
MFA drastically reduces account-takeover attempts, even when credentials are stolen.
2. Use a Password Manager to Avoid Fake Login Pages
Password managers auto-fill credentials only on legitimate domains—an excellent defense against redirect-based phishing.
3. Train Employees to Recognize Facebook-Themed Phishing
Focus on:
- Avoiding clicking unexpected “policy violation” messages
- Verifying links by navigating directly to Facebook.com
- Reviewing business page email alerts carefully
- Questioning messages that create urgency
- Double-checking external-link warnings
4. Monitor Business Pages and Ad Accounts for Changes
Facebook Business accounts should be monitored just like any other business-critical platform. Watch for:
- New admins added
- Sudden ad spending changes
- Suspicious page posts
- Security or recovery email changes
5. Use Simulated Phishing to Reinforce Awareness
Social-media-themed phishing simulations help employees practice identifying deception.
Platforms such as PhishingBox let organizations send realistic training scenarios that mimic actual Facebook scams—helping reduce real-world risk.
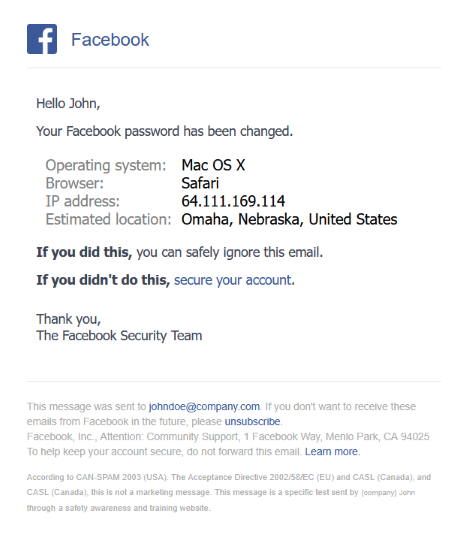
Example of a PhishingBox Facebook-themed phishing template used in user awareness training.
Conclusion
The latest Facebook phishing scams demonstrate how quickly attackers adapt. What used to be simple credential-stealing pages has evolved into sophisticated redirect abuse, impersonation of Meta business infrastructure, and high-volume campaigns targeting advertisers and organizations.
By combining MFA, password managers, internal monitoring, and regular phishing awareness training, individuals and businesses can significantly reduce the risk of compromise.




