January 2026: Recent Threats & Social Engineering Trends
A breakdown of 2026’s top social engineering threats, including phishing, vishing, AiTM attacks, and credential exposure—and how to reduce risk.
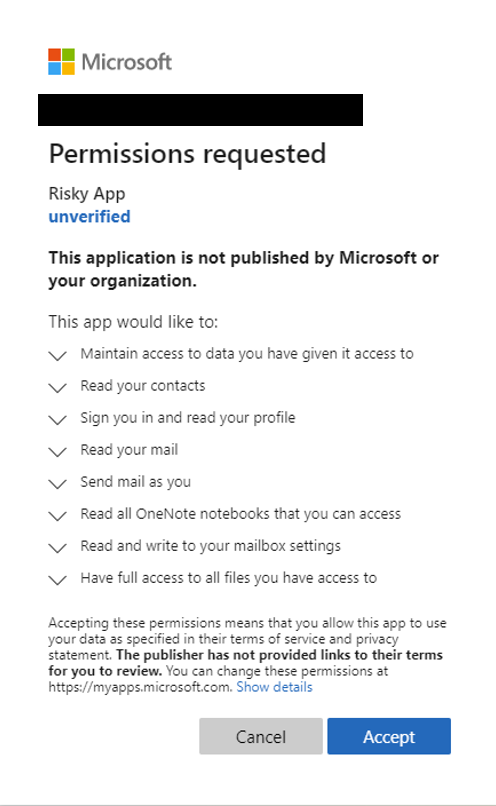
A new post by the Microsoft security team warns about a new type of phishing attack vector targeting users. Consent Phishing, as they refer to it as, targets users by asking for an egregious amount of permissions from Single-Sign-On allowing the bad actors to abuse the accounts they have been granted access to.
Taking advantage of the shift of a large number of employees from working in the office to working from home, attackers have begun abusing the increased need of employees to download and use cloud based applications. These applications often use Single-Sign-On resulting in a false sense of security from those who use the easy to use single click to sign up or install the application. These one click installations grant access to a variety of permissions that can be abused by bad actors and range from sending emails on users behalf, access to a users contact list, to having access to all files that a user has and the ability to create, modify, or delete them.
The potential for abuse is obvious if one of these compromising applications gets access to a user, and therefore must be protected against. While steps can be made to defend against users installing or connecting their accounts to these applications, understanding how the attack works and sharing that information can be an effective way to help train employees to recognize when they are being targeted.