The Rise of Phishing-as-a-Service
Phishing kits are becoming one of the most accessible components within a cybercriminal's arsenal.
Improve security with phishing simulation and ongoing cybersecurity training for employees.
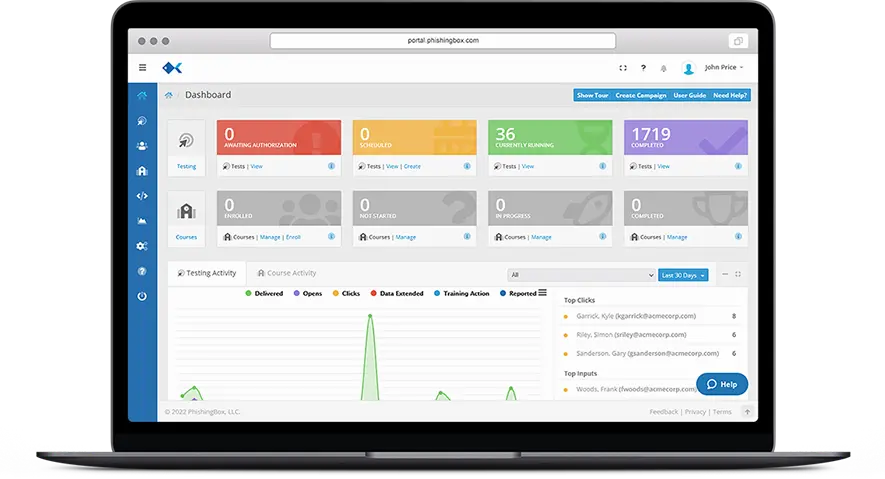
Establishing a robust security awareness training program is a necessity in today's cybercrime-prone environment. Security threats and compliance mandates require ongoing security awareness training for most organizations. With the PhishingBox suite of software tools, an organization can establish a sound employee security awareness program.
PhishingBox integrates with several popular third-party, cloud-based services.
Save time and money with pre-built phishing emails and other advanced tools.
No training needed to conduct social engineering testing.
Save time and resources through the menu-driven system.
Get the data you need to identify security weaknesses.
Use one system to easily conduct testing for multiple clients.
Let us do the heavy lifting so you can stay focused on building your business.