Meaningful, relevant, current training content establishes a solid foundation for your general user base and simulated phishing campaigns provide insight and create opportunities for risk mitigation.
Optiv Security Training
No matter how advanced your security technology is, every organization has risk associated with its workforce. Human risk is difficult to quantify because stakeholders must consider every type of threat: malicious, negligent, and unwitting. Investing in a holistic program to educate and empower everyone who touches your network inherently reduces the risk by increasing awareness and impacting culture. Optiv offers a comprehensive approach to cybersecurity education through both general end user awareness and role-based training. Meaningful, relevant, current training content establishes a solid foundation for your general user base and simulated phishing campaigns provide insight and create opportunities for risk mitigation.
Learn
We work with your stakeholders to identify appropriate general end user and role-based training providing meaningful business impacts and personal relevance to end users.
Experience
Create an environment of awareness outside of formalized training with reinforcement materials like newsletters, posters, digital images, and simulated phishing campaigns.
Transform
Cybersecurity education programs are more than just content – they're a strategy. Transform your organization’s culture into one of awareness and ownership through positive behavior change.
Sample Training Pages
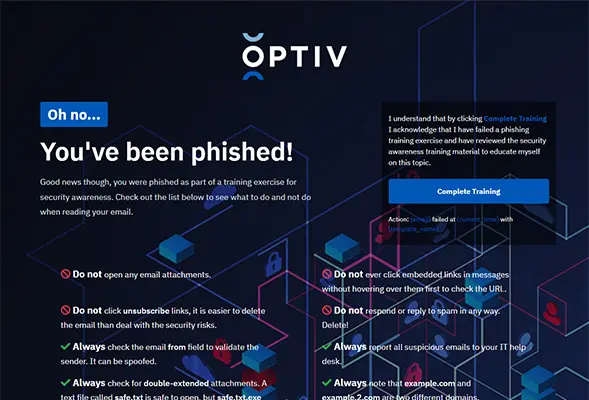
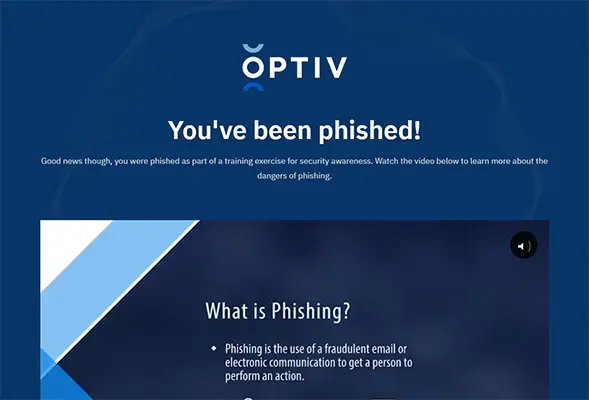
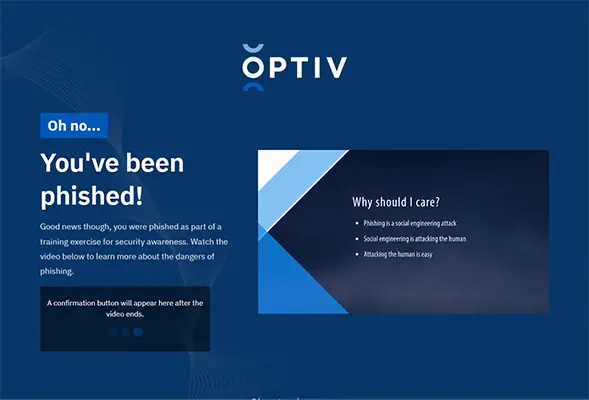
After a user clicks on a phishing campaign they will be shown a training page. Below are a few training pages using Optiv content.