A premier global cybersecurity awareness & simulated phishing training solution that uses engaging, 3-to-4 minute Hollywood-style microlearning videos to educate and empower individuals and organizations to become defenders against cyber threats.
NINJIO Security Training
NINJIO is a premier global cybersecurity awareness & simulated phishing training solution that uses engaging, 3-to-4 minute, Hollywood-style microlearning videos to educate and empower individuals and organizations to become defenders against cyber threats. According to Gartner's Peer Insights "Voice of the Customer" report for 2021, NINJIO has been designated as the only "Voice of the Customer" in the computer-based training solutions market out of 42 total vendors covered by Gartner.
Animated Episodes
NINJIO produces 3-to-4 minute, micro-learning episodes to educate your users on the latest threats and breaches. NINJIO releases a new episode every month, which keeps your team up to date.
Real Attacks
Every episode is based on a real company that has suffered a significant breach. NINJIO focuses on a single attack vector to not overwhelm your employees with technical terms.
Hollywood Writing
Each episode is written by a member of the Writers Guild of America who has written and produced a combined total of 72 episodes for CSI: NY and Hawaii Five-0.
Training Offers
NINJIO serves some of the largest companies in the world and has changed the behavior of hundreds of thousands of people through engaging, emotionally-driven storytelling.
NINJIO Aware Anime
NINJIO AWARE™ ANIME uses American anime cartoon characters to educate users about cybersecurity awareness. This video format uses NINJIO’s signature Hollywood-style storytelling to shape the behavior of employees, staff, and team members to raise the security bar in the office and at home.
NINJIO Aware Corporate
NINJIO AWARE™ CORPORATE uses a more conservative style of animation and character sets compared to NINJIO AWARE™ ANIME. No matter the style, each episode is derived from the same topic, script, and voice acting, with the only difference being different character styles.
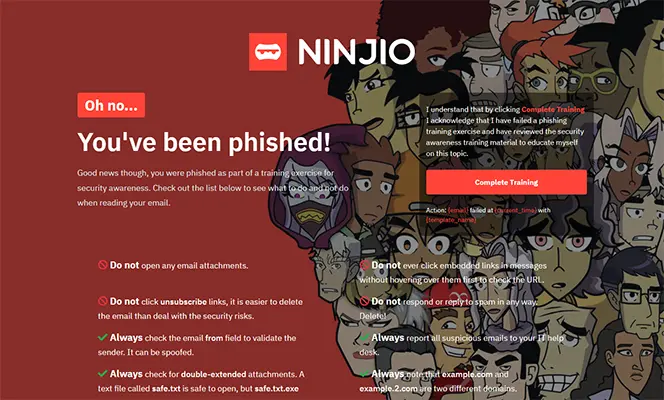
Sample Training Pages
After a user clicks on a phishing campaign they will be shown a training page. Below are a few training pages using NINJIO content.