Programs that effectively promotes cybersecurity behavior change, protects your organization, and strengthens the human element.
Global Learning Systems Security Training
Global Learning Systems (GLS) started nearly 30 years ago, combining two former subsidiaries: Electronic Learning Facilitators (ELF), developers of award-winning, custom learning solutions, and Keystone Learning, pioneers of video-based, web-hosted software and business-skills training products. Today GLS combines its 30 years of experience providing employee security awareness and compliance training programs with a unique OnDemand Learning Management System. Their program effectively promotes cybersecurity behavior change, protects your organization, and strengthens the human element.
Experience
With over 30 years of experience developing behavior change programs, GLS training experts have designed off-the-shelf learning products focused on changing high-risk employee behaviors.
Award-winning
Cybersecurity GLS has been recognized in the Gartner Magic Quadrant for Security Awareness Computer-based Training for five consecutive years.
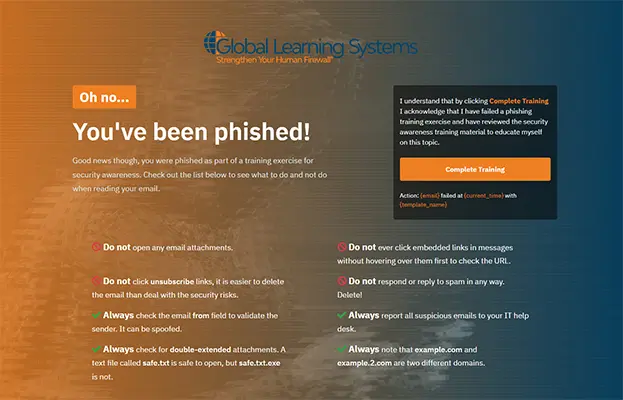
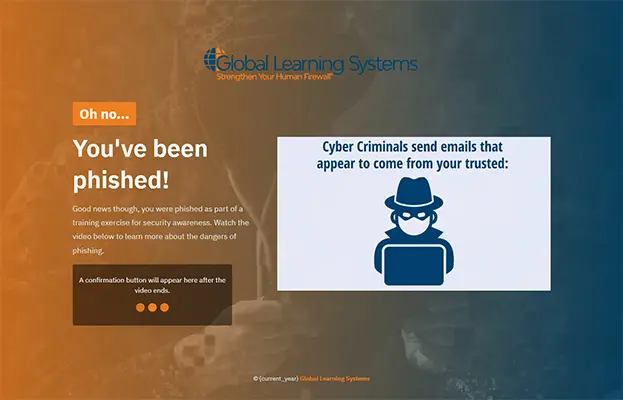
Sample Training Pages
After a user clicks on a phishing campaign they will be shown a training page. Below are a few training pages using Global Learning Systems content.