As reported by
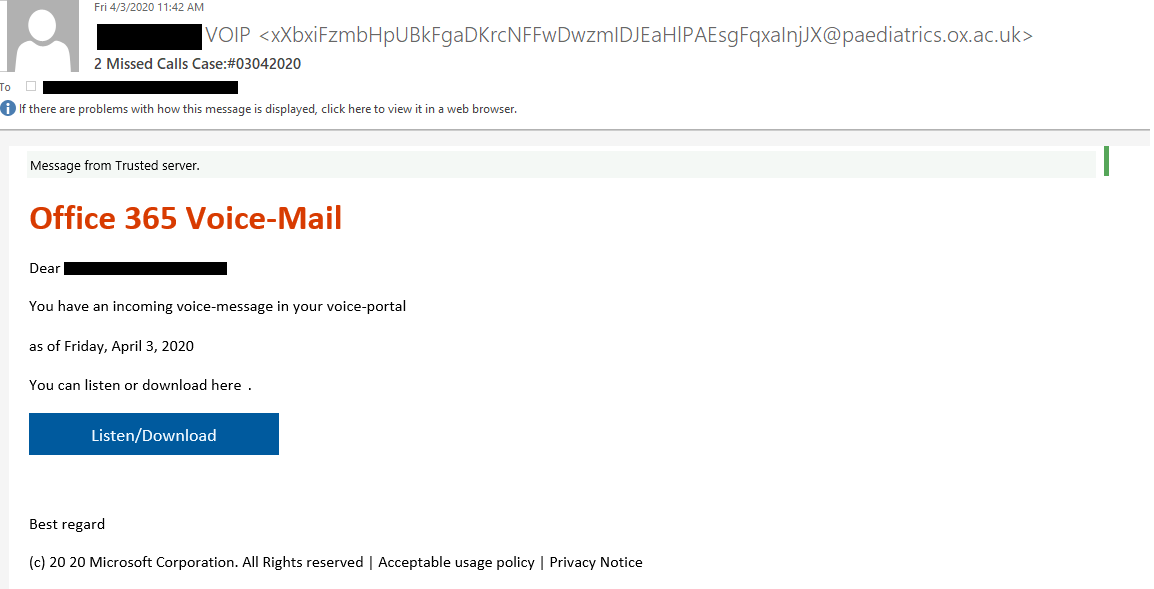
Checkpoint Research, European users of Office 365 have been targeted with phishing emails sent from seemingly legitimate sources after bad actors hijacked Samsung's Adobe Campaign marketing redirect mechanism to send missed voicemail emails to targets which were able to get the "Message from Trusted Server" at the top of the email due to the combined trusted nature of Oxford, Samsung, and Adobe. Once the link was clicked, targets were taken to an Office 365 themed website and requested that they sign into their accounts to access the voicemail. By using a trusted domain from Oxford to send the emails and an Adobe marketing link from Samsung which then redirected users to the landing page, the attackers were able to take advantage of Office 365 being unable to tell that the email was not trustworthy resulting in their "Message from Trusted Server" at the top of the email while distancing their phishing site from the email.
Compromised SMTP Server
In order to have the email come from a trusted source, the attackers found a way to abuse Oxford SMTP server to send emails from as many email addresses as they wanted. Once they had gained the ability to send from the SMTP server, they were able to auto-generate addresses which appeared to be from different departments so as to not appear suspicious when sending emails. Emails that appeared to look like an Office 365 email were then used to trick recipients into clicking on the link within the email.
Abusing Marketing Redirecting Links
The link in the email was a modified marketing link from Samsung which used the Adobe Campaign platform. Normally used to track conversions and links, the attackers were able to replace the appended URLs' within the redirect link with their own link. Using an older Cyber Monday link, the attackers used the redirect to point recipients towards a compromised WordPress sites which then redirected them again to their own landing page which copied the Office 365 login page.
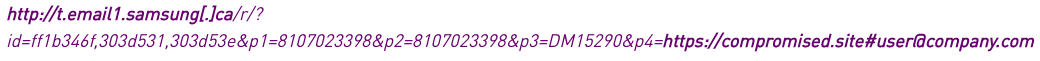
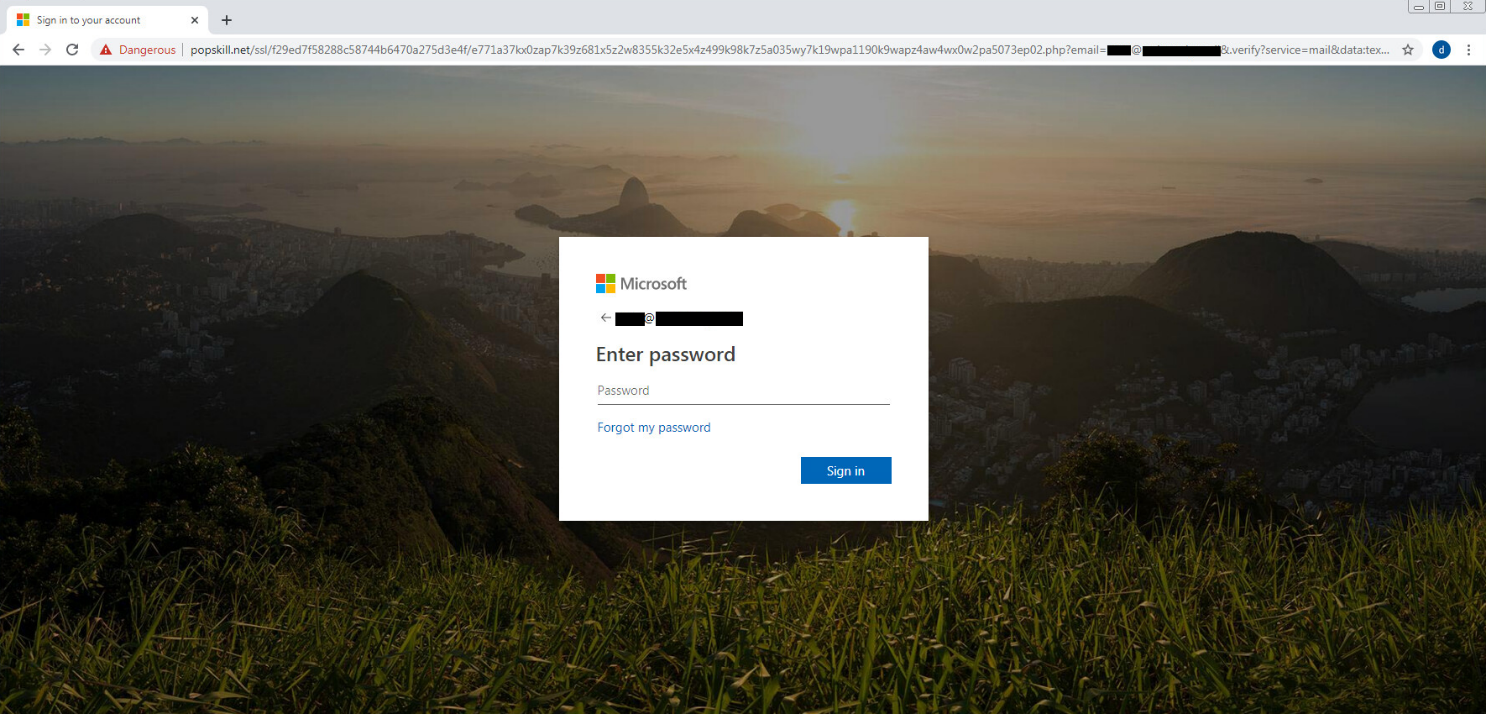
While Adobe was worked to fix the issue of being able to hijack their marketing links, this style of attack goes to show how training your employees with strong security awareness and regularly testing them could help prevent employees form clicking on links such as this. If employees are trained correctly, they would not click on the link within their email, and instead go to the correct domain by typing it into their browser and signing in while being secure in their knowledge that the site can not be compromised by navigating to the real domain.