As is common with real phishing campaigns, bad actors are using current events to take advantage of people and trick them into opening malicious emails. While the last few months have been dominated by COVID-19 related phishing emails, a new phishing campaign, discovered by Abuse.ch and first reported
here has begun taking advantage of the Black Lives Matter movement in an attempt to install malware.
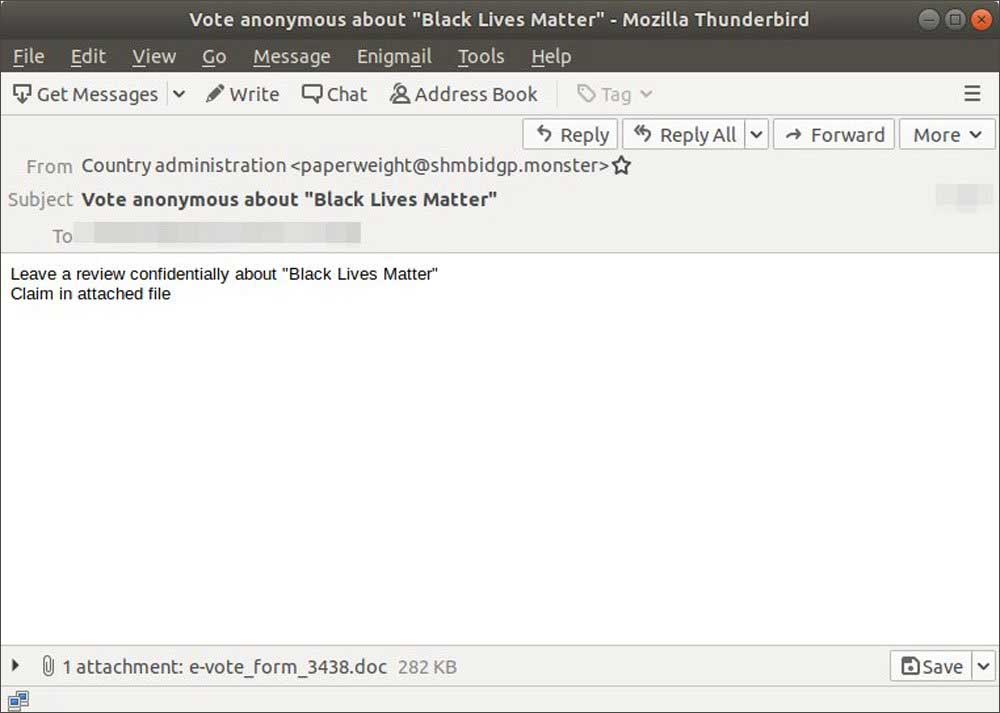
Pretending to be from "County administration", the email subject line asks people who are targeted in the attack to 'Vote anonymous about "Black Lives Matter". The body of the email says "Leave a review confidentially about "Black Lives Matter" and then prompts recipients to "Claim in attached file" a document named 'e-vote_form_3438.doc.'
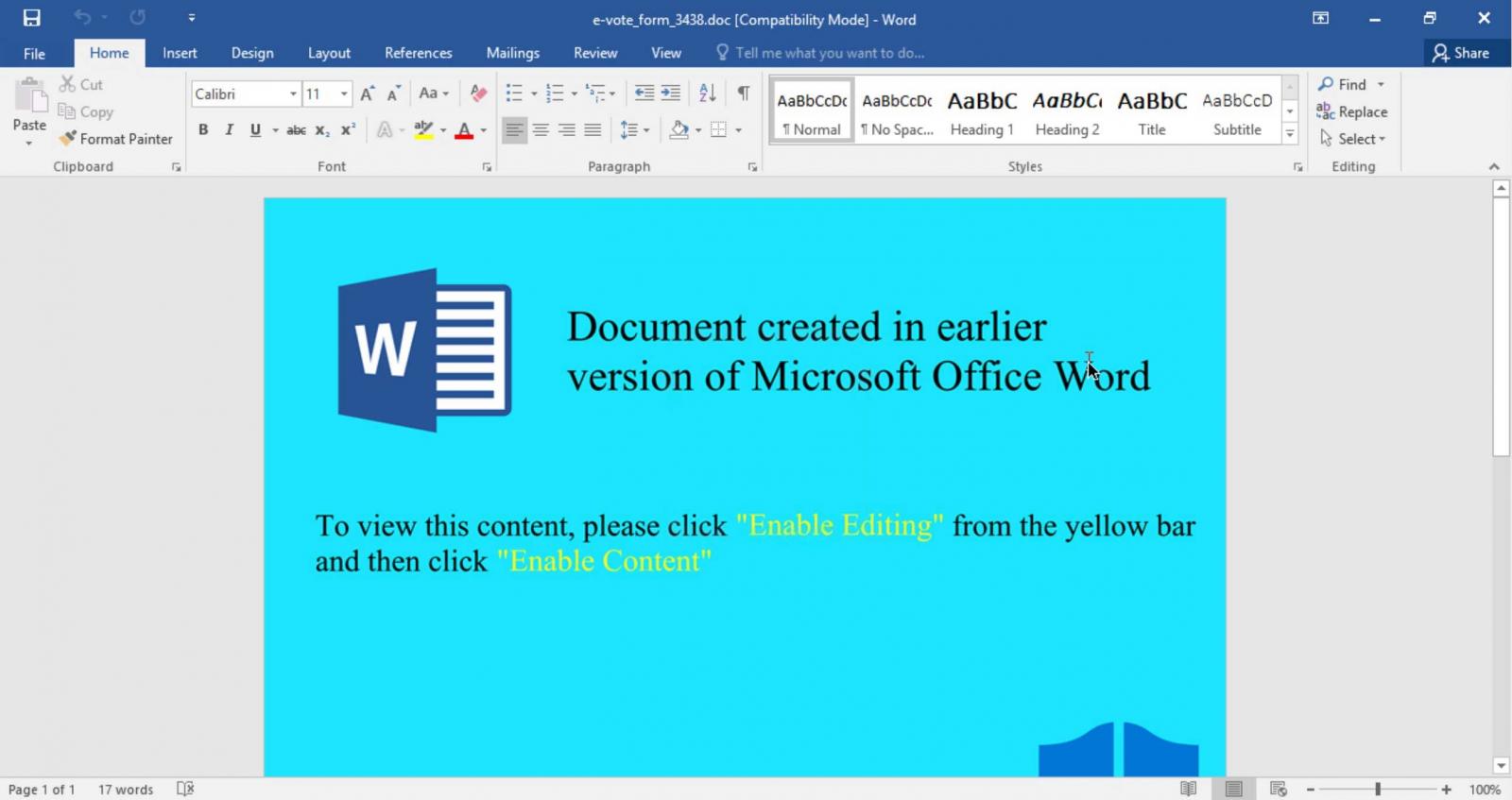
The attachment opens a Word Document which directs them to "Enable Editing" and "Enable Content". By doing so, the document begins to run macros to download a malicious DLL and execute the TrickBot malware. Once executed, TrickBot downloads more modules which steal files, passwords, and security keys throughout the network, as well as allow the installation of ransomware.
Phishing Attack Simulation and Security Awareness Training for your employees is more important than ever due to the significant increase in attacks from current events. Taking advantage of the news and pretending to act as groups such as Black Lives Matter can have a significant impact in tricking employees into succumbing to phishing emails.